Prepare Bootable Media
Installing Ubuntu on a new computer is straightforward. First, prepare a bootable USB stick or SD card. On another machine running Ubuntu download the latest OS image and save it to a local file. Then run Startup Disk Creator. Click on the Other button on the opening screen to navigate to the image.
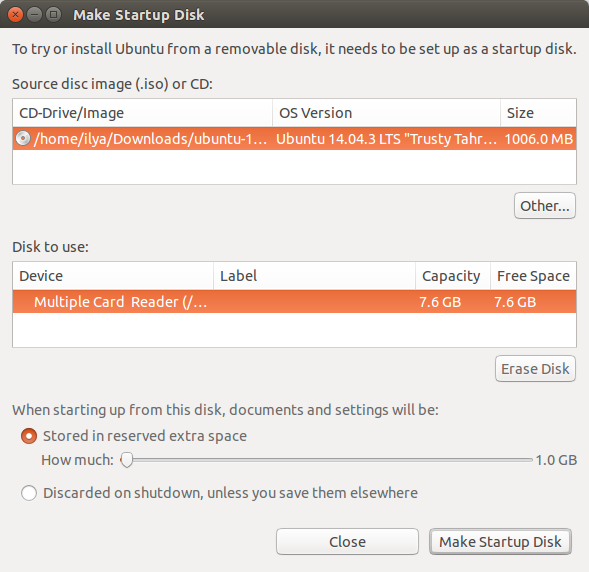
Select target USB device and click Make Startup Disk.
Installation
I suggest booting Ubuntu from a USB device prior to installation to make sure that all system components are visible to the operating system. In particular, make sure that storage devices can be used. Run Disk application to check if the target device is visible.
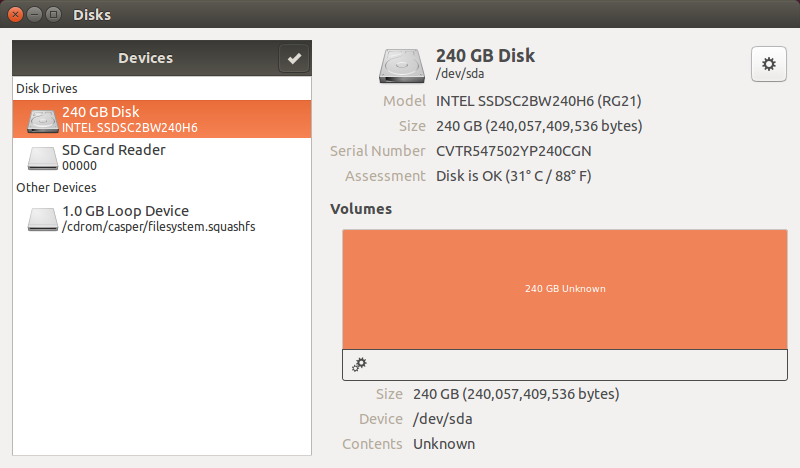
Run Install Ubuntu application. By default it will create three partitions on target disk drive: EFIboot, Linux filesystem, and Swap.
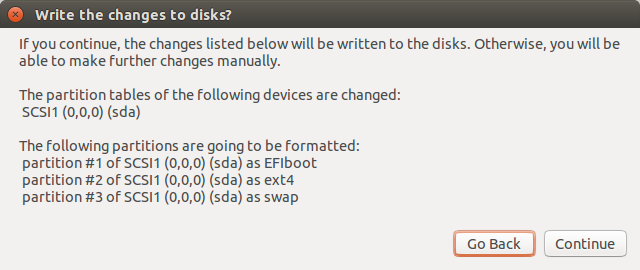
Default breakdown will work fine. On my system with 16GB of RAM and 240GB SSD the Linux partition takes 222GB, Swap takes 17GB and EFIboot is less than a gigabyte.
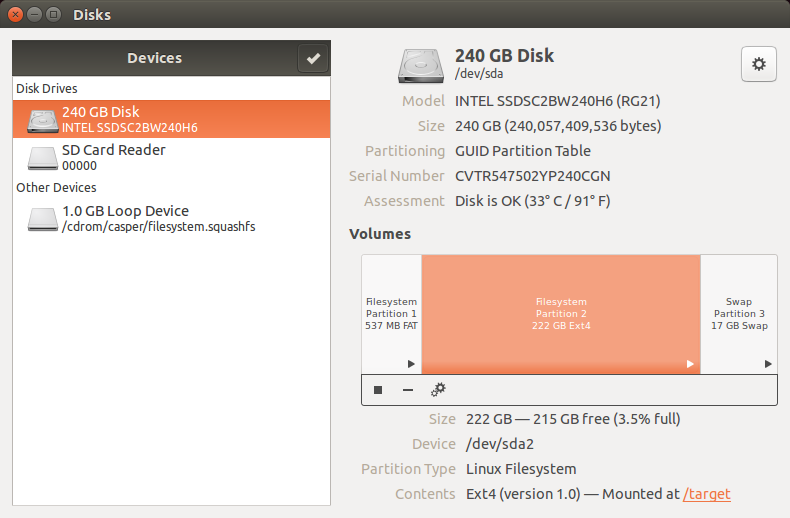
Once installation completes, reboot the system and it is ready to go.
The user account created during installation has superuser privileges but it’s also handy to have access to the root account. To set the password for root just run passwd under sudo.
ilya@ilya-ubuntu:~$ sudo passwdIf you want to keep the PATH environment settings from your user account when you use sudo you can edit the settings in /etc/sudoers:
root@lin1:~# diff /etc/sudoers /etc/sudoers.orig
9,11c9,11
< #Defaults env_reset
< #Defaults mail_badpass
< #Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin" --- > Defaults env_reset
> Defaults mail_badpass
> Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"To run sudo commands with the same LD_LIBRARY_PATH as the user account one can explicitly pass it as a parameter:
$ sudo LD_LIBRARY_PATH=$LD_LIBRARY_PATH pip install -U scikit-learnor include an alias in the the ~/.bashrc file:
alias sudo='sudo LD_LIBRARY_PATH=$LD_LIBRARY_PATH'In either case one should ensure that PATH and LD_LIBRARY_PATH don’t point to directories with malicious code as it wreak havoc on the system if executed with superuser privileges.